In an era where remote work and digital learning have become the standard, the need for transparency and security within computing environments has never been more critical. Whether for a business owner ensuring team productivity or a parent safeguarding their children’s online experience, sentrypc.com offers a robust, cloud-based solution. By combining real-time monitoring with strict content filtering and time management, sentrypc.com provides a centralized hub to oversee digital behavior across multiple devices, ensuring that technology is used responsibly and efficiently.
The Power of Cloud-Based Stealth Monitoring
What makes the product at sentrypc.com special is its completely cloud-based architecture and its ability to operate in total stealth. Once the software is installed on a target device, it can run invisibly in the background without alerting the user. This is particularly valuable for businesses conducting sensitive internal investigations or parents who want to observe natural online behavior without the interference of “monitored behavior” bias. Because sentrypc.com is managed via the cloud, administrators can log in to their secure dashboard from any web-enabled device to view logs or change settings in real-time, eliminating the need to physically access the monitored computer again.
Comprehensive Management Tools and Features
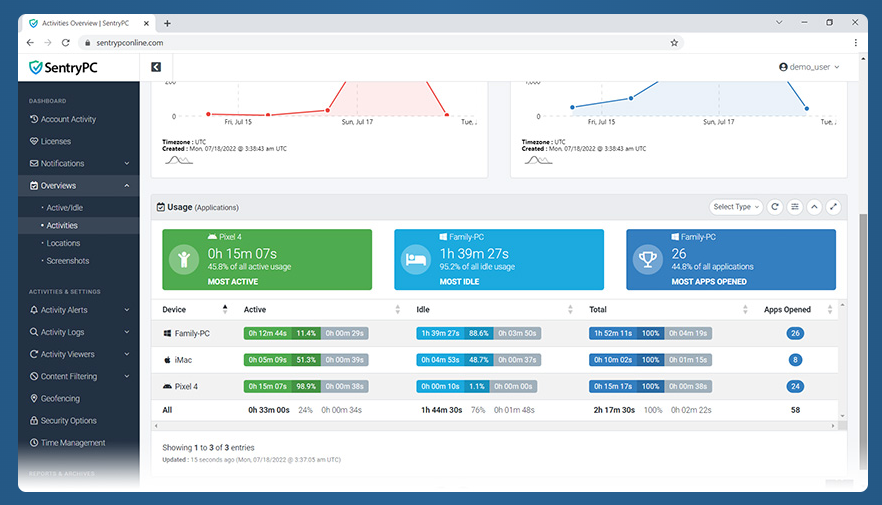
When navigating the sentrypc.com website, users will find a detailed breakdown of its multifaceted toolkit. The platform is designed to be a “set-and-forget” system that handles the heavy lifting of data collection. Key features available include:
- Real-Time Activity Logging: sentrypc.com records virtually every action, including keystrokes, website visits, application usage, and even file transfers.
- Visual Screenshot Capturing: Beyond text logs, the software can capture screenshots at specific intervals or when certain “trigger” keywords are typed, providing visual context to the recorded data.
- Time Management and Scheduling: Administrators can set strict usage limits, defining exactly which hours of the day a user can access the device or the internet, which is a vital feature for preventing employee burnout or managing a child’s screen time.
- Geofencing and Location Tracking: For mobile Windows tablets or laptops, sentrypc.com can track the physical location of the device and alert the administrator if it leaves a predefined geographical area.
Key Differences Between This Platform and Other Brands
The primary differentiator for sentrypc.com is its aggressive focus on affordability and scalability. Many competitors in the employee monitoring space require a high minimum number of licenses or charge significant monthly fees per user. In contrast, sentrypc.com offers a low-cost entry point with annual plans that are often a fraction of the price of enterprise-level software. This makes sentrypc.com particularly attractive for small businesses, startups, and individual families who need professional-grade tools on a modest budget.
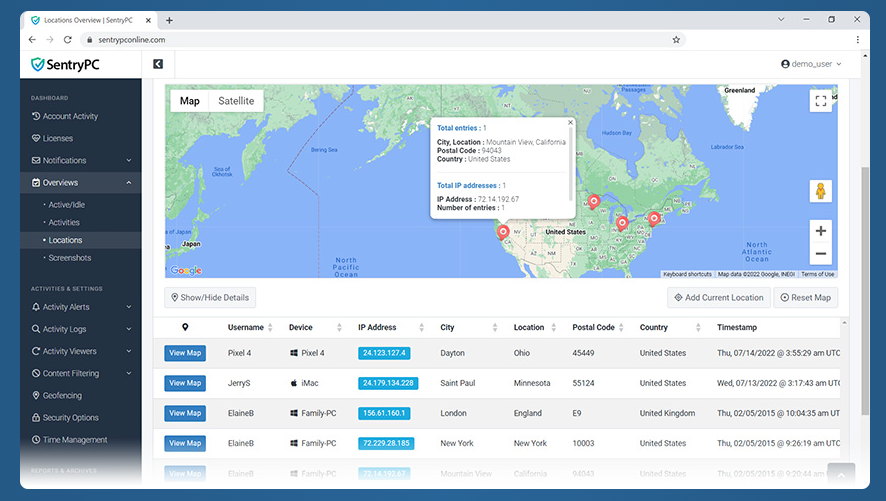
Furthermore, unlike brands that focus exclusively on monitoring, sentrypc.com integrates proactive prevention. Its content filtering engine allows for the blocking of entire categories of websites—such as social media, gambling, or adult content—and can even prevent specific applications or games from launching. This dual-action approach—monitoring what has happened while simultaneously preventing what shouldn’t happen—is what sets sentrypc.com apart from passive logging tools.
A Scalable Solution for Modern Infrastructure
Whether you are managing a single home computer or a fleet of hundreds of workstations spread across different locations, sentrypc.com scales effortlessly. The installation process is streamlined for rapid deployment via email or local network, and the platform supports Windows, Mac, Chromebook, and Android operating systems. By centralizing the management of these diverse devices into one intuitive interface, sentrypc.com reduces the administrative burden on IT managers and parents alike, providing clear, actionable insights into how technology is being utilized within their organization or home.